U.S. cyber plan calls for private-sector scans of Net
Posted: 22 March 2013 Filed under: Uncategorized | Tags: privacy, security Leave a commentU.S. cyber plan calls for private-sector scans of Net
The Department of Homeland Security will gather the secret data and pass it to a small group of telecommunication companies and cybersecurity providers that have employees holding security clearances, government and industry officials said. Those companies will then offer to process email and other Internet transmissions for critical infrastructure customers that choose to participate in the program.
By using DHS as the middleman, the Obama administration hopes to bring the formidable overseas intelligence-gathering of the NSA closer to ordinary U.S. residents without triggering an outcry from privacy advocates who have long been leery of the spy agency’s eavesdropping.
Very perceptive mannequins
Posted: 28 November 2012 Filed under: Uncategorized | Tags: privacy Leave a commentWow. So… some mannequins spy on you.
In the lead-up to the holiday shopping season, BusinessWeek reported that “bionic mannequins are spying on shoppers to boost luxury sales” at five unnamed companies. The $5,130 EyeSee mannequins from Almax have cameras embedded in their eyes that use IBM Cognos software to record the number of shoppers checking out window displays and clothes, while also noting their age, gender and race. They don’t keep any images of the customers, just the aggregate data about who’s been considering blowing money on cashmere sweaters and $300 jeans. But it may not stop there.
“To give the EyeSee ears as well as eyes, Almax is testing technology that recognizes words to allow retailers to eavesdrop on what shoppers say about the mannequin’s attire,” reports BusinessWeek. This is the second time I’ve heard a business float the idea of recording customers’ conversation in order to better advertise to them. The desire for better marketing may just be the biggest threat out there to your privacy.
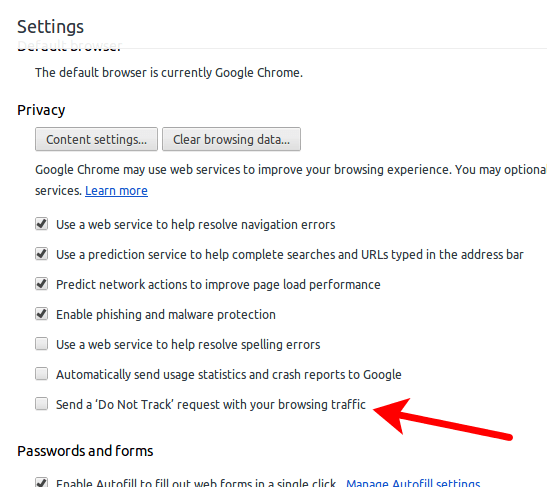
Do Not Track in Google Chrome
Posted: 7 November 2012 Filed under: privacy | Tags: privacy Leave a commentShows the “Do Not Track” option in Google Chrome v.23 and up.
To turn this on, click Chrome’s Settings menu | Show advanced settings… | Privacy | “Send a ‘Do Not Track’ request with your browsing traffic.”
Facebook using Datalogix tracking
Posted: 25 September 2012 Filed under: Uncategorized | Tags: privacy Leave a commentDatalogix has purchasing data from about 70m American households largely drawn from loyalty cards and programmes at more than 1,000 retailers, including grocers and drug stores. By matching email addresses or other identifying information associated with those cards against emails or information used to establish Facebook accounts, Datalogix can track whether people bought a product in a store after seeing an ad on Facebook.
http://edition.cnn.com/2012/09/23/business/facebook-datalogix/
Interesting.
Silent Circle’s privacy-enhancing service expected to launch later this year
Posted: 20 June 2012 Filed under: privacy | Tags: privacy, security Leave a commentThe need for privacy-enhancing technologies continues. If all our communications are routinely intercepted and scrutinized, some of us will need the assurance that our good work is done without observance. Certain countries don’t like human rights workers “poking around,” for instance, or want to closely observe the movements of aid agency observers.
With that in mind, Phil Zimmermann, the original brain behind PGP, expects to launch Silent Circle later this year. The company’s main offering is a $20-a-month encryption service for voice, SMS, videoconference and e-mail traffic.
Life insurers deciding whether to use tracked Web data
Posted: 29 August 2011 Filed under: privacy | Tags: privacy, user tracking Leave a commentInteresting. So apparently I missed that life insurers are looking at using tracked Web data (such as that collected by Acxiom) to evaluate whether or not to insure people. Of course Acxiom says that it “wouldn’t” share this info with insurers, but it makes more sense to me that they would follow the money instead, changing their rules if necessary.
Acxiom recently told investors it takes in three billion pieces of information daily as businesses seek to “monetize” information about their customers. Some retailers share information about purchases made by people, including item description, price and the person’s name.
Increasingly, information comes from people’s online behavior. Acxiom says it buys data from online publishers about what kinds of articles a subscriber reads—financial or sports, for example—and can find out if somebody’s a gourmet-food lover from their online purchases. Online marketers often tap data sources like these to target ads at Web users.
User-friendly PKI: not yet
Posted: 12 November 2010 Filed under: security | Tags: gpg, pgp, pki, privacy, security 2 CommentsPublic-key infrastructure is great. When it works, you can be quite sure that you are communicating with whom you want to communicate, and you can even communicate securely if you wish. Alice and Clare can send each other mail, and Bob won’t be able to sneak in there and read it.
It’s supremely easy for Alice to create a private key, and publish her public key to a keyserver. “That’s it?” she thinks, with a leap of her heart. “Wow! It’s so easy!”
Let’s fast-forward a bit.
For a while, Alice and Clare have fun sending encrypted messages back and forth. They find a plug-in to send encrypted mail through their GMail accounts (FireGPG), and that’s useful for a while, although oops, the developer discontinues GMail support. But they can still use other clients, and they do so.
Things are hunky-dory for a while.
Then one day Alice upgrades her computer, and she forgets to migrate her private key over to the new box. She doesn’t have her passphrase at hand, of course, because she had her e-mail client save it for her; she had it on a sticky note so she only had to look it up once in a while.
“Oh, well,” thinks Alice. “I’ll just create a new public key.”
Oops. Is this user-friendly?
Now Alice has a PGP key sitting out there on a keyserver. She can’t use it because she doesn’t have the equivalent private key. She can’t revoke it because she didn’t think it was that important to create a revocation certificate at the time and save it. Someone told her to do that once. “Don’t save it in the cloud, but on a disk that would never lose its data and could never be compromised. Then lock it away in a safe in your basement. You did make sure your basement was a Faraday cage, didn’t you?”
PKI is such a useful, powerful tool. But… it’s still very easy to screw up and cause lasting damage, though. I guess it’s like a “Hole Hawg,” an apt comparison to other powerful technologies, as noted by Neal Stephenson.
There IS an option for Alice. She can create a new key, with a user ID like: “only use this key. That other one is bad,” and then get all her friends to sign the new key. There are other techniques, but that’s pretty much as close as she’s going to get.
Questions like this in security-related topics interest me: If it’s easier to use, will more people use it? And if it’s more widely used, will that increase its relevance?